Advertiser Disclosure
We test the top contenders to identify those offering the best Mac antivirus protection. Bottom Line: Latest software reviews, specification match up, price comparisons, editor and user ratings. Jun 11, 2020 Mac Internet Security X9 provides top-notch antivirus protection against the latest threats, and is rated up there with the best (like Bitdefender and Kaspersky) when it comes to the independent.
✓ Protection from all malware for Mac
✓ No impact on the speed of Macbooks
✓ Best deals and lowest prices
Find the best antivirus for: Windows | Mac
Norton 360 (new)
The most complete antivirus for Mac.Antivirus, firewall, VPN and a password manager.
- Protection for Mac100%100%
- Speed100%100%
✓ Protects Windows, Mac, iOS and Android
✓ 60-day money-back guarantee
✓ VPN: Free and unlimited
Read our full Norton Review
BitDefender for Mac
Perfect protection, but no extra features. It has antivirus and a VPN, but not much more.
- Protection for Mac100%100%
- Speed100%100%
✓ 30-day money-back guarantee
✓ VPN: Free but limited to 200 mb
Read our full BitDefender Review
Avast
Perfect protection scores, but at a heavy performance cost. Significantly slows down your Mac.
- Protection for Mac100%100%
- Speed58%58%
✓ 30-day money-back guarantee
✓ VPN: Not included for free
Read our full Avast Review
The Best Antivirus of the Year
Millions of users around the world trust Norton as the industry leader in antivirus technology
How We Test
Below we explain with factors go into the calculation of our editors’ rating, what each of these factors mean, and the data sources we use
How We Test
Finding the right antivirus for mac is crucial. To make sure you have the right tools to make the decision, we want to be as transparent in our analysis as possible.
We use 6 criteria to analyze the winning programs. All criteria matter, but not all are equally important. Therefore, they impact the final score in different degrees. Below we show you the 6 factors and the impact they have.
- Protection from Malware50%50%
- Impact on Performance and Speed15%15%
- Devices and Features10%10%
- User Reviews10%10%
- Value for Money10%10%
- False Positives5%5%
Our protection, performance and false positive data comes from AV-Test and AV-Comparatives. These are considered the two global leaders in cybersecurity software testing.
Our user review data comes from TrustPilot and Google’s App Store, called Google Play. TrustPilot specializes in the collection of verified user reviews in a central location. Google Play, in turn, is the app database for Android users. It has one of the largest software review databases in the world.
The Supported Devices data is taken directly from the vendors. And finally, value for Money represents the relation between the requested price and the protection and features offered, of which all data comes from the vendors.
Test Factors and Sources:
Protection from Malware
Protection from malware makes up 50% of the total score
Protection from malware and other online threats is the most important feature of any cybersecurity product.
Malware is a term used to describe a vast quantity of digital attacks. These include viruses, spyware, ransomware, adware, phishing, rootkits, keyloggers, and many more. As you can imagine, protecting users from such a diverse set of threats requires a diverse set of methods.
Over time, three distinct protection methods have developed and evolved. Each of the top ranking antiviruses has been tested extensively according to these. We describe each in more detail below.
Signature File Detection:
The classic form of malware detection, often referred to as virus scanning. In this method, antivirus programs scan files for digital signatures of malware. These digital signatures can be viewed as patterns, in either activity or code, that indicate the presence of malware.
Each malware has a unique digital signature which is stored in an incredibly large database containing hundreds of millions of malware samples. Whenever a cybersecurity firm discovers a new malware, its sample is added to the database.
This method has many advantages. It is fast, reliable, relatively easy to operate and scalable. But it is not perfect. As it can only discover known malware threats that have been uploaded to the database, it is blind to discovering new malware attacks.
To combat this, cybersecurity companies have evolved their methods. Using machine learning, they have developed the next stage in malware discovery: Heuristic file detection.
Heuristic File Detection:
Heuristic file detection is designed to discover malware threats that have never been encountered before and do not exist in any database.
To find these new threats, the antivirus software looks at behavioral patterns rather than signatures. This means it scans files and systems for particular suspicious activities that are common to malware.
When these patterns are uncovered, the antivirus software has two more methods of analyzing the suspicious files further:
File Emulation: File emulation is commonly referred to as sandbox testing. Using this method, the antivirus software executes the potential malware in a safe environment in which it cannot cause harm. This is often a virtual machine, called the sandbox.
In this environment, the antivirus program can analyze the suspicious file for common malware practices without any risk. These practices include the deletion of files, rapid replication in the system or network, and any attempt to hide specific files in the operating software.
Once it is confirmed that the suspicious file is indeed malware, further action will be taken to eliminate the threat.
Genetic Signature Detection: Developing malware is not an easy task, and malware creators like to reuse their creations as often as possible. Therefore, these cybercriminals frequently create slightly adjusted versions of their malware that are just unique enough to pass the signature-based detection method.
Genetic signature detection is developed to protect users from these slightly adjusted forms of malware. In this method, the source code of suspicious files is compared to the source code of known malware in the database. If a certain percentage of the source code overlap, the file is considered malware and further action will be taken to eliminate the threat.
User-Focused Protection Features:
In a constant game of cat and mouse, both malware and anti-malware technologies are evolving rapidly. They have come to the point where both are so sophisticated that it is often easier for malware creators to use a different route: Targeting the user directly.
There are many forms of malware, such as phishing, social engineering, scams, and identity theft, that don’t necessarily include the use of malicious software. Instead, these are clever schemes developed to trick users into providing cybercriminals with sensitive information.
The best antivirus programs for Mac have developed a range of clever tools to protect users from these schemes. Among many others, these include:
Website advisors: A tool that warns you before you access a website known for malicious intent.
WiFi security advisors: A tool that advises you on the safety of a specific WiFi network and whether using a VPN would be a wise choice.
Password managers: Tools designed to generate and store highly unique and secure passwords. They also automatically log you in on your favorite websites when you visit them.
Encrypted browsers: Browsers with an added layer of security that automatically launch when you access payment and banking websites.
Impact on Performance and Speed
Performance impact makes up 15% of the total score
If your Macbook slows down because antivirus software is running in the background, we speak of a negative performance impact. This can be measured in website load times, download speeds or the CPU resources required to run the software.
Devices and Features
Supported devices makes up 10% of the total score
For this factor, we investigate the supported devices per antivirus software. On top of that, we analyze which features are offered for each of the antivirus software. Often, a full security solution is offered for Windows, but the antivirus for Android, and Mac are far less generously equipped.
A note on iOS:
All antivirus providers create software for Windows, Mac, and Android. For Mac, however, not all do so with equal dedication. Some top-rated antivirus companies, such as Panda, BullGuard, and McAfee for instance, do not participate in the testing of their antivirus for Mac products by the IT security institutes. Which is also why they are not included in the line up of the best antivirus software for mac.
On top of that, not all antivirus providers offer security apps for iOS. Although It is true that iOS is a safer platform than the other operating software, this is only the case with malware. As ever more consumers fall into phishing traps, use insecure passwords, and surf unencrypted public wifi networks, even iOS users should have a cybersecurity app.
User Reviews
User Reviews make up 10% of the total score
User reviews are an important factor in the analysis of any potential purchase. They not only represent product satisfaction, but also the overall customer experience a user has in the engagement with the company.
Sadly, however, user reviews are easily faked and it’s difficult to know which sources to trust. We therefore only use review data from the most credible sources available: TrustPilot and the Google Play Store.
Value For Money
Value for Money makes up 10% of the total score
The damage caused by malware can be very significant. Both emotionally and financially. We therefore believe the price of an antivirus product should not be the most important factor in your purchasing decision.
That being said, it definitely has a role to play. As there are vendors that simply offer significantly more value for money than others, It pays to shop around and make a well-information purchasing decision.
To help you, we have analyzed the global pricing strategy of each firm to find out which offers the most value for your buck.
False Positives
False Positives makes up 5% of the total score
When a clean file is flagged as malware, we speak of a false positives. This is fairly common when using the heuristic file detection method and nothing to worry about. However, some antivirus programs generate significantly more false positives than others, which can be annoying.
Data Sources
AV-Test is one of the leading test organizations in cybersecurity. Based in Germany, they have been performing in-depth antivirus analysis since 2013. AV-Test uses an incredibly large database of malware samples and state-of-the-art technology to run their tests. We consult the reports of AV-Test in the calculation of the performance and protection scores.
AV-Comparatives is the second top test organization in cybersecurity. Based in Austria, they have been running their software analysis since 1999. AV-Comparatives is famous for the creation of real-world test scenario’s that are capable of testing every aspect of the antivirus software. We consult their reports for the calculation of the performance and protection scores.
TrustPilot is the international leader in B2C (business to consumer) reviews. Over 200.000 companies have been reviewed on their platform by over 45 million reviews.
The Google Play Store is the app store for Android, the most used mobile operating system in the world. The Google Play Store has one of the largest software review databases in the world.
Tibor Moes
Technology analyst
Tech enthusiast and founder of SoftwareLab. He has degrees in Engineering and Business, and has been active in the analysis of software, electronics and digital services since 2013.
Navigate this page
- How we test?
Done reading?
Visit Norton for a unique SoftwareLab discount.
Navigate this page: Top 5 Antivirus | How We Test | Frequently Asked Questions
Frequently Asked Questions
Below we have summed up the most commonly asked questions surrounding the topic of cybersecurity and the best antivirus software.
What Is Adware?
Adware is freely distributed software that contains and displays built-in advertisements for various products and services. It is also a type of software that can redirect queries to various sponsor websites. Another facet of adware software is data collection, which is usually done for marketing purposes.
This type of software, depending on how complex it is, can collect search history results, keystrokes, keywords, search patterns, and sometimes even personal information, most often without the user’s consent. Adware doesn’t always have to be installed manually. It can be installed remotely on a user’s computer when they visit an infected website. Hackers can also install malicious adware via a backdoor.
What Is Antivirus?
Antiviruses are among the most important lines of defense of computers and other internet-enabled devices. Antivirus programs or program suites are designed to detect threats, quarantine them, remove them, as well as prevent them from accessing the target computer or network in the first place.
Depending on the complexity of the antivirus software, it can protect against low-key and high-risk attacks and invasions of privacy such as those made possible by hacking, viruses, worms, adware, rootkits, spyware, keyloggers, and others. While sandbox detection techniques are the most popular, various detection algorithms are implemented today, the most modern of which use data mining and machine learning.
What Is a Botnet?
A botnet is a network of hijacked internet-connected devices that can be used for their superior combined computing power to deliver powerful attacks, disrupt internet traffic, or send spam. In a botnet, the hijacked computers are infected with bots, software programs that can perform automated tasks. Each computer in the network can operate one or more bots.
Also known as a zombie army or a zombie network, a botnet can be used by its owner through C&C software. Some threat actors may choose to use botnets for their own DDoS attacks, while others may rent out the botnet to interested third parties with malicious intent of their own.
What Is a Computer Exploit?
Various command sequences, as well as pieces of software, code, and data may fall under the category of computer exploits when they are used to exploit certain software or hardware vulnerabilities on foreign devices or networks. Depending on the vulnerability, a computer exploit can be assigned to a specific subtype, all contingent on what the exploit can do to a foreign system thanks to the vulnerability it takes advantage of.
Exploits can be local and remote. Remote vulnerabilities allow varying degrees of access remotely while local vulnerabilities usually imply than an exploit cannot be used unless the origin of the attack comes from within the vulnerable device or network. This too can sometimes be accessed remotely if there is backdoor access into the system.
What Is a Computer Virus?
A computer virus is usually a self-replicating malicious code that can copy itself into new programs, documents, or boot sectors, thus altering the way in which a device works. Computer viruses can be spread knowingly or unknowingly, but they need to be activated on the target device to have any effect. That’s why many viruses are embedded into software that looks trustworthy and legitimate or hidden inside links to websites that are seemingly legit.
There is also a risk of transmission through infected storage devices such as USB drives. Viruses can target system memory or core functions of apps and hardware components. They can also be designed to copy or delete data, or even encrypt it, which is something that’s often used in ransomware.
What Is a Computer Worm?
A computer worm is a subclass of computer viruses that rarely requires any help from the user (i.e. opening a program) to self-replicate and propagate itself in a vast network of interconnected devices. Worms usually get into a system either by direct download or through an unprotected network connection. Once inside a system, a worm can replicate itself multiple times and spread to other devices.
Although worms are sometimes viewed as a less threatening subclass, they are also often used to install backdoors into systems. These backdoors can then be used to install other malicious malware like keyloggers, adware, spyware, or bots, as well as to lay the foundation for a DDoS attack.
What Is Computer Hacking?
Computer hacking, or just hacking, is any unauthorized intrusion into a computer or computer network. Such actions usually involve compromising the system security by either altering some of its features or bypassing security measures altogether to achieve anything from access to confidential information to establishing root access to that system.
The term hacking doesn’t always imply negative activities. While there are people who use their skills to hack into foreign systems for personal, financial, or political gain, there are also those who hack into systems only to test their security and discover flaws or exploits. As a result of this type of hacking, many vulnerabilities can be patched before malicious hackers can exploit them.
What Is Cybercrime?
For a crime to qualify as a cybercrime, it needs to either target a computer or use a computer as a tool to commit the offense. Although there are various subtypes of cybercrime, they can all be categorized into two larger types – crimes that target individual computers or networks and those that target the device owners.
Some of the most common types of cybercrime include bank information theft, identity theft, cyberterrorism, online predatory crimes, and online stalking. Not all cybercrimes are end-game actions. Some of them are simply one small step in a much larger scheme that extends to the offline world as well.
What Is a DDoS Attack?
A DDoS attack is most often carried out by a botnet or zombie army of computers. It stands for distributed denial-of-service attack. The terminology refers to the disruption of services – either of a network or, say, a website. This is achieved by flooding target devices with unwanted internet traffic that hampers their performance.
The most common targets for DDoS attacks are online vendors, marketplaces, as well as other businesses that depend on having a stable connection and cannot afford to lose bandwidth. DDoS attacks may not only slow the performance of the targeted system but can also corrupt data or lead to data loss, not to mention significant financial losses.
What Is Identity Theft?
Identity theft is used to describe any unauthorized gathering of personal identifying information, achieved by any means, physically or in the virtual world. Identity theft can be done via shoulder-surfing, stealing bank statements, obtaining fingerprints, dumpster diving, and so many more methods. The perpetrator uses this information to assume the victim’s identity and gain personal benefit.
In this day and age, identity theft is more often than not classified as a cybercrime due to the fact that it involves hacking computer networks and databases for private information. It can also be done via spyware, keyloggers, planting viruses, email phishing, and other types of actions classified as cybercrimes.
What Is a Keylogger?
There are two types of keyloggers. There are hardware keyloggers and software keyloggers. Regardless of which one is used, the main goal is always the same: tracking someone’s keystrokes in order to monitor and record whatever it is they’re doing on a device, whether they’re browsing the internet, writing emails, writing code, etc.
Keyloggers are not always used with malicious intent. They can be used in cognitive writing research, to monitor employees on their work computers, or monitor underage kids and their online activities. However, they tend to have a negative connotation since they’re most often used as standalone tools or part of advanced rootkits to steal confidential information or grant access to target devices.
What Is Malware?
The term malware (short for malicious software) denotes all harmful pieces software such as computer viruses and worms, Trojans, ransomware, and adware, among others. Cybercriminals use it to establish a backdoor into foreign systems, create botnets, and launch various attacks for the purpose of stealing, corrupting, or deleting data on the target systems.
A malware suite, or a collection of more than one types of malicious software, is often referred to as a rootkit. Multiple types of covert malware programs can be embedded in a single application or file.
What Is Phishing?
Mac Antivirus Software Reviews
Phishing is a fraudulent act that involves the theft of credit card numbers, usernames, passwords, and other sensitive information in which a criminal poses as a trustworthy individual or business. Over the internet, phishing usually involves the use of fake websites with seemingly trustworthy domain names.
Although quite dangerous, phishing is usually easily avoidable if the user exercises more caution when opening attachments, disclosing their personal information, checking website URLs, and using up-to-date antivirus software. Phishing can’t be successful without some involuntary help from the victims themselves, hence the need for cybercriminals to impersonate legitimate entities when phishing for information.
What Is Ransomware?
Ransomware is a type of malware that is most often associated with holding certain files, data, or financial assets hostage. This malware can be remotely installed via a backdoor or downloaded by the user from infected websites or attachments. Once inside the target’s system, the malware encrypts information that cannot be decrypted without a key. Other designations for ransomware include crypto-Trojan, crypto-worm, or crypto-virus.
Ransomware is also sometimes used to steal information. As a result, it is used in online blackmailing schemes in which the victim is threatened with the release of potentially compromising personal information that’s been encrypted by the hacker unless a ransom is paid off. Finding the source of the attack or the attacker is generally very difficult since most ransoms involve cryptocurrency payouts.
What Is a Rootkit?
Rootkits are usually, but not always, malware suites comprised of multiple programs and viruses designed to grant access to a computer or computer network by secretly exploiting various system vulnerabilities. Rootkits can be distributed via attachments, adware, email links, and other means.
The most common goal for a rootkit is establishing a backdoor access to the target system, which will allow the attacker to easily steal information, documents, money, or passwords. The perpetrator can also use this to wreak havoc on the system by corrupting data, disrupting traffic, deleting data, or slowing down the system’s performance. Modern antivirus programs have rootkit detection, whereas this was a much more difficult problem to deal with in the past.
What Is a Scam?
A scam is a fraudulent and criminal action initiated by an individual or group of individuals for the purpose of extracting sensitive information, stealing money, repurposing goods, etc. Internet scams include fake donations, cold calls, chain mail, online surveys, and many more.
A large majority of scams are done via the internet due to the ease of access that scammers have to networks of people. Some scams are quick schemes with a well-defined goal while others are larger cons that involve multiple steps in establishing trust, obtaining sensitive information, and stealing money.
What Is Social Engineering?
In the context of computer security, social engineering involves the use of psychological manipulation of individuals and groups using various techniques. Regardless of the specific technique that is used, social engineering is often employed with malicious intent and for the purpose of stealing confidential information or disrupting the normal operation of certain organizations.
Phishing is one aspect of social engineering as it involves tricking the target into revealing sensitive information. However, social engineering involves both low-tech and high-tech methods of manipulating victims. Just like with phishing, the perpetrator aims to earn the victim’s trust in order to gain access to information they can use to either harm the target or gain something for themselves.
What Is Spam?
Sending spam (also known as spamming) is the action of sending multiple unsolicited electronic messages. Spam almost always has a negative connotation but isn’t always part of some illegal scheme. Spam email, for example, can simply be part of an aggressive advertising campaign for certain products or services.
On the other hand, spam email can also be used in phishing schemes. In that case, the emails likely contain infected attachments or links to fake versions of various legitimate websites. Their creators’ goal is to collect personal information that can be used to extort money or information from the victim, gain access to restricted servers, or steal one’s identity.
What Is Email, IP, or DNS Spoofing?
Email spoofing is done to gain access to confidential information from an individual or groups of individuals. This type of action involves creating fake versions of legitimate websites that look good enough at first glance, to convince the target to reveal whatever information is requested.
DNS spoofing can be a standalone scam or part of an email spoofing scan. It involves diverting traffic from trusted websites to fake versions of those websites, from which the website owners can get the victims’ personal identifying information, usernames and passwords, credit card information, etc.
IP spoofing is not always used with malicious intent. Some people use IP spoofing and VPN services to access georestricted websites or hide their online activities. However, it can also be used to gain access to restricted networks in order to steal information or carry out some other malicious activities.
What Is Spyware?
Spyware is a subclass of malware programs that may include keyloggers, adware, Trojans, system monitors, tracking cookies, and other programs designed to monitor, record, and steal information. Most spyware programs are designed to operate covertly, without the user’s knowledge or consent. They can be standalone programs, remotely installed, or programs that need to be triggered by an action on the end-user’s device.
Spyware may collect a wide range of data or very specific information from targeted devices. In the case of adware, it may simply collect marketing-related information. In the case of keyloggers, however, it can steal usernames, passwords, identifying bank credentials, and so much more.
What Is an SQL Injection Attack?
An SQL injection attack is any action that inserts malicious SQL code into an SQL database for the purpose of gaining access to data and modifying, corrupting, or deleting it. It can either be done for financial gain or to wreak havoc on someone’s business, thus causing significant economic damage.
Most SQL injection attacks are directed towards online vendors and online marketplaces. However, due to the constant attacks against the e-commerce sector, there are more than a few ways to secure and protect websites with SQL databases against these attacks. Today, very little damage can be done to protected systems, thanks to the advanced antivirus and firewall programs available for small businesses and large enterprises.
What Is a Trojan Horse?
A Trojan horse, also known as a Trojan virus or simply Trojan, is a type of computer virus that can cause harm to a system once activated. Unlike a computer worm, a Trojan requires activation on the end-user’s system to do its job. However, this is not a type of virus that self-replicates and spreads to other systems.
Most of the time, a Trojan virus is used to establish backdoor access or remote access into the target system. Some Trojans are used to steal information directly or to download other malicious software onto the target computer or network.
What Is a Zero-Day Exploit?
A zero-day exploit, sometimes called a zero-hour exploit is not one particular exploit but rather a category of computer exploits. It includes all unknown or recently discovered computer exploits. Any exploit that’s known only to the attacker and is used to take advantage of a vulnerability is called a zero-day exploit.

These exploits are virtually impossible to defend against, because they are inconspicuous and work thanks to undiscovered or unpublicized vulnerabilities in various apps or networks. Once such an exploit has been made public, it is called an N-day exploit, with N being the number of days since the exploit was first discovered and since developers have started working on fixing it.
Navigate this page: Top 5 Antivirus | How We Test | Frequently Asked Questions
Sources
Below you can find all the sources we have used in our analysis
AV-Test:
https://www.av-test.org/en/antivirus/mobile-devices/android/july-2019/
https://www.av-test.org/en/antivirus/mobile-devices/android/may-2019/
https://www.av-test.org/en/antivirus/mobile-devices/android/march-2019/
https://www.av-test.org/en/antivirus/mobile-devices/android/january-2019/
https://www.av-test.org/en/antivirus/mobile-devices/android/november-2018/
https://www.av-test.org/en/antivirus/mobile-devices/android/september-2018/
https://www.av-test.org/en/antivirus/mobile-devices/android/july-2018/
https://www.av-test.org/en/antivirus/mobile-devices/android/may-2018/
https://www.av-test.org/en/antivirus/mobile-devices/android/march-2018/
https://www.av-test.org/en/antivirus/mobile-devices/android/january-2018/
https://www.av-test.org/en/antivirus/mobile-devices/android/november-2017/
https://www.av-test.org/en/antivirus/mobile-devices/android/september-2017/
https://www.av-test.org/en/antivirus/mobile-devices/android/july-2017/
https://www.av-test.org/en/antivirus/mobile-devices/android/may-2017/
https://www.av-test.org/en/antivirus/mobile-devices/android/march-2017/
https://www.av-test.org/en/antivirus/mobile-devices/android/january-2017/
https://www.av-test.org/en/antivirus/home-macos/macos-mojave/june-2019/
https://www.av-test.org/en/antivirus/home-macos/macos-high-sierra/december-2018/
https://www.av-test.org/en/antivirus/home-macos/macos-high-sierra/june-2018/
https://www.av-test.org/en/antivirus/home-macos/macos-sierra/december-2017/
https://www.av-test.org/en/antivirus/home-macos/macos-sierra/june-2017/
https://www.av-test.org/en/antivirus/home-windows/windows-10/august-2019/
https://www.av-test.org/en/antivirus/home-windows/windows-10/june-2019/
https://www.av-test.org/en/antivirus/home-windows/windows-10/april-2019/
https://www.av-test.org/en/antivirus/home-windows/windows-10/february-2019/
https://www.av-test.org/en/antivirus/home-windows/windows-10/december-2018/
https://www.av-test.org/en/antivirus/home-windows/windows-10/october-2018/
https://www.av-test.org/en/antivirus/home-windows/windows-10/june-2018/
https://www.av-test.org/en/antivirus/home-windows/windows-10/april-2018/
https://www.av-test.org/en/antivirus/home-windows/windows-10/december-2017/
https://www.av-test.org/en/antivirus/home-windows/windows-10/october-2017/
https://www.av-test.org/en/antivirus/home-windows/windows-10/june-2017/
https://www.av-test.org/en/antivirus/home-windows/windows-10/april-2017/
https://www.av-test.org/en/antivirus/business-macos/macos-mojave/june-2019/
https://www.av-test.org/en/antivirus/business-macos/macos-high-sierra/december-2018/
https://www.av-test.org/en/antivirus/business-macos/macos-high-sierra/june-2018/
https://www.av-test.org/en/antivirus/business-macos/macos-sierra/december-2017/
https://www.av-test.org/en/antivirus/business-windows-client/windows-10/june-2019/
https://www.av-test.org/en/antivirus/business-windows-client/windows-10/april-2019/
https://www.av-test.org/en/antivirus/business-windows-client/windows-10/february-2019/
https://www.av-test.org/en/antivirus/business-windows-client/windows-10/december-2018/
https://www.av-test.org/en/antivirus/business-windows-client/windows-10/october-2018/
https://www.av-test.org/en/antivirus/business-windows-client/windows-10/august-2018/
https://www.av-test.org/en/antivirus/business-windows-client/windows-10/june-2018/
https://www.av-test.org/en/antivirus/business-windows-client/windows-10/april-2018/
https://www.av-test.org/en/antivirus/business-windows-client/windows-10/february-2018/
AV-Comparatives:
https://www.av-comparatives.org/tests/mobile-security-review-2019/
https://www.av-comparatives.org/tests/mobile-security-review-2018/
https://www.av-comparatives.org/tests/mobile-security-review-2017/
https://www.av-comparatives.org/tests/mac-security-test-review-2019/
https://www.av-comparatives.org/tests/mac-security-test-review-2018/
https://www.av-comparatives.org/tests/mac-security-test-review-2017/
https://www.av-comparatives.org/tests/performance-test-april-2019/
https://www.av-comparatives.org/tests/performance-test-october-2018/
https://www.av-comparatives.org/tests/performance-test-april-2018/
https://www.av-comparatives.org/tests/performance-test-october-2017/
https://www.av-comparatives.org/tests/real-world-protection-test-february-may-2019/
https://www.av-comparatives.org/tests/real-world-protection-test-july-november-2018/
https://www.av-comparatives.org/tests/real-world-protection-test-october-2018-factsheet/
https://www.av-comparatives.org/tests/real-world-protection-test-february-june-2018/
https://www.av-comparatives.org/tests/real-world-protection-test-july-november-2017/
https://www.av-comparatives.org/tests/malware-protection-test-march-2019/
https://www.av-comparatives.org/tests/malware-protection-test-september-2018/
https://www.av-comparatives.org/tests/malware-protection-test-march-2018/
https://www.av-comparatives.org/tests/malware-protection-test-september-2017/
https://www.av-comparatives.org/tests/business-security-test-2019-march-june/
https://www.av-comparatives.org/tests/business-security-test-march-april-2019-factsheet/
https://www.av-comparatives.org/tests/business-security-test-2018-august-november/
https://www.av-comparatives.org/tests/business-security-test-2018-march-june/
https://www.av-comparatives.org/tests/malware-removal-test-2018/
TrustPilot:
https://www.trustpilot.com/review/www.bitdefender.com
https://www.trustpilot.com/review/www.bitdefender.de
https://www.trustpilot.com/review/bitdefenderofficial.com
https://www.trustpilot.com/review/www.norton.com
https://www.trustpilot.com/review/dk.norton.com
https://www.trustpilot.com/review/www.mcafee.com
https://www.trustpilot.com/review/pandasecurity.com/france
https://www.trustpilot.com/review/pandasecurity.com/germany
https://www.trustpilot.com/review/pandasecurity.com/netherlands
https://www.trustpilot.com/review/www.pandasecurity.com
https://www.trustpilot.com/review/pandasecurity.com/spain
https://www.trustpilot.com/review/www.bullguard.com
Google Play:
https://play.google.com/store/apps/details?id=com.bitdefender.security
https://play.google.com/store/apps/details?id=com.symantec.mobilesecurity
https://play.google.com/store/apps/details?id=com.wsandroid.suite
https://play.google.com/store/apps/details?id=com.avast.android.mobilesecurity
https://play.google.com/store/apps/details?id=com.pandasecurity.pandaav
https://play.google.com/store/apps/details?id=com.bullguard.mobile.mobilesecurity
About Us | Contact Us | Cookie Policy | Privacy Policy | Terms of Use
SoftwareLab.org is operated by Momento Ventures Inc. © 2020. All rights reserved.Disclaimer: SoftwareLab.org is not an antivirus, VPN or hosting service provider and does not endorse the use of the products featured on this website for unlawful means. It is the responsibility of the user to adhere to all applicable laws. We have no control over the third-party websites we link to and they are governed by their own terms and conditions. SoftwareLab.org is supported by advertisement in order to be a free-to-use resource. We strive to keep the information accurate and up-to-date, but cannot guarantee that it is always the case.
Software
Pros
- Top scores from one independent testing lab.
- Speedy full scan.
- Attractive, lightweight user interface.
Cons
- Phishing protection not yet working.
Bottom Line
Newcomer Airo Antivirus for Mac earns top scores from one testing lab and has a refreshing Mac-centric interface, but some of its components aren't yet ready.
The proliferation of cross-platform security suite products has resulted in a Mac antivirus boom, as each vendor wants to promise protection on Windows, macOS, Android, and iOS. Few companies focus specifically on macOS, and even fewer new Mac-specific products show up. It's refreshing, therefore, to see the arrival of Airo Antivirus for Mac on the market. This newcomer earned some impressive lab scores, and its attractive, lightweight design should appeal to Mac enthusiasts. However, it's on the expensive side, and not all components are working yet as of this writing.
Pricing and OS Support
You pay $49.99 per year for a single Airo license. Upping that to $69.99 gets you three licenses, and $89.99 brings the total to five. Originally I reported prices of $69.99, $99.99, and $129.99, since these were visible (though struck out) on the pricing page. My company contact pointed out that those prices are never used, and proved it by removing them from the pricing page. I'm glad; the product looked rather expensive before that fix.
Intego costs $99.99 for three licenses, while ClamXAV (for Mac) costs just $29.99 for three. Like Airo, Intego and ClamXAV are specific to the macOS platform. In the cross-platform realm, you get five Norton licenses for $99.99, along with five no-limits licenses for Norton's VPN.
You can try Airo for a week at no cost, with no need to give any personal details. That's a nice touch, but a few macOS antivirus products are entirely free. You don't have to pay a thing to protect your Mac with Avira, Avast, or Sophos. Even ignoring these free options, Airo is on the high side, price-wise. The most common price-point for a single license is $39.99; that's what you pay for Bitdefender, Kaspersky Internet Security for Mac, ESET, Trend Micro, and Webroot.
Between $45 and $65 for three licenses is another sweet spot; Bitdefender, ESET, Kaspersky, ProtectWorks, Vipre, and Webroot all fall in that range. And for $59.99 per year, McAfee AntiVirus Plus (for Mac) lets you install protection on every Windows, macOS, Android, or iOS device in your household.
Like Avira, Sophos, and Vipre, Airo supports macOS versions 10.11 (El Capitan) and later. Trend Micro really wants you up to date; it only supports 10.13 (High Sierra) and later. If legacy software or antique hardware requires you to stay with an old macOS version, you might consider ProtectWorks AntiVirus (for Mac) or ClamXAV, both of which go all the way back to 10.6 (Snow Leopard). Webroot also handles dated systems, with support back to 10.7 (Lion).
Getting Started With Airo
Once you've purchased your license and created your Airo account, you simply download and install the product. It quickly grabs the latest build from Airo's servers. The installer walks you through granting necessary permissions, such as full disk access to remove malware, and it offers to explain why it needs each permission. It also offers to add phishing protection to your browser. When the installer has finished, it cheerily announces, 'All is good in the world. Airo has been installed.'
Airo aims for a light footprint. It doesn't appear in the dock. Rather, you pull down its distinctive tall, skinny window from its icon in the menu bar at top whenever you need it. The main Status page just reports on the latest scan and latest update, with a big button to launch a scan. A Threats page lets you review malware threats that the product found and quarantined. Another page holds the product's few configuration settings. The fourth and final page lets you manage your account.
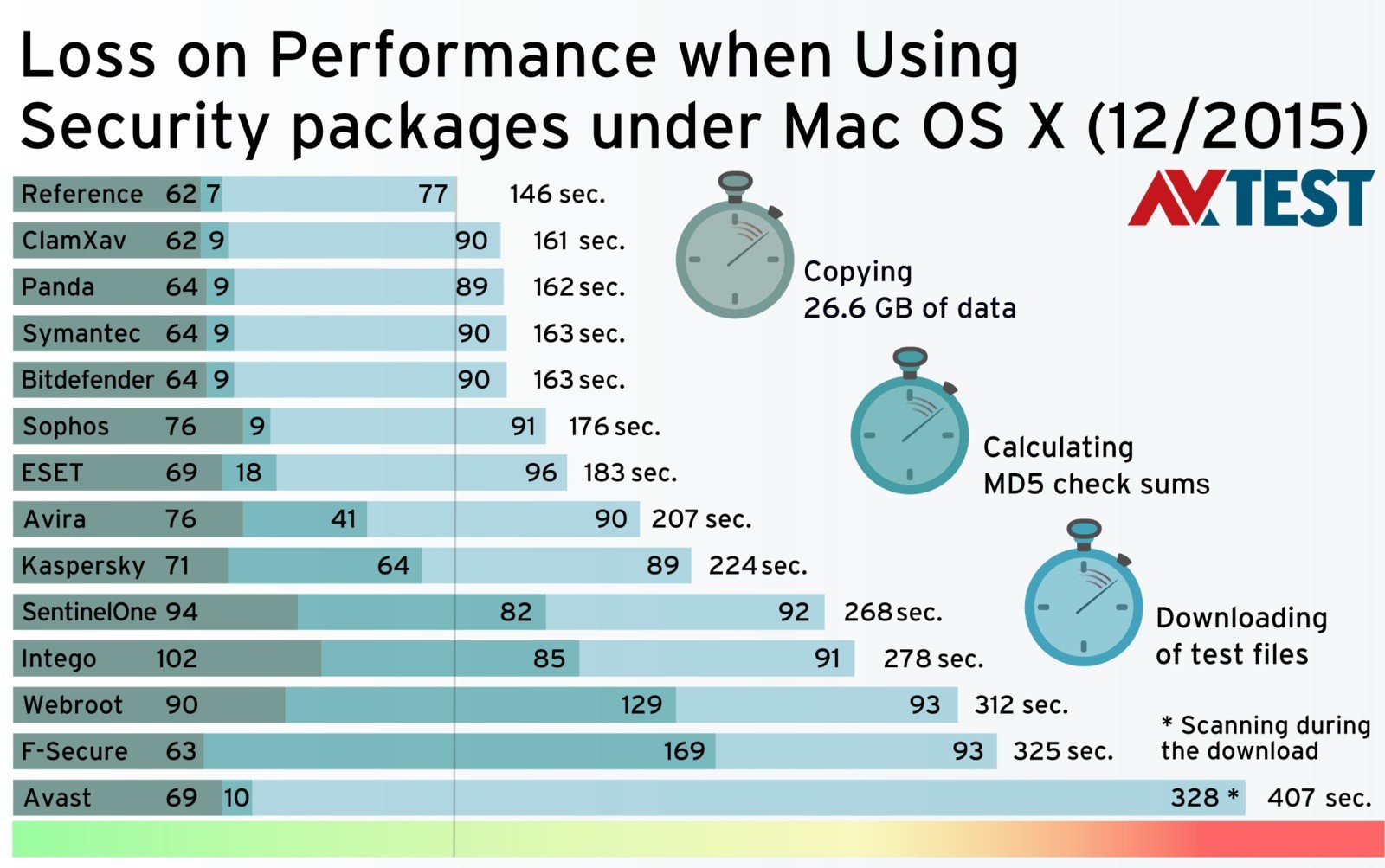
The product prompted me to run a quick scan, so I indulged it. That scan finished in barely 20 seconds. Then I clicked the hard-to-see Scan Options link and launched a full scan, which also finished quickly, 11 minutes. Trend Micro came in slightly faster, at 10 minutes. Webroot SecureAnywhere Antivirus (for Mac) is the fastest macOS scanner I've timed, finishing its full scan in just 2.5 minutes.
Hands On With Airo
Just about every Mac-focused antivirus also tries to wipe out any Windows malware it encounters. Naturally these foreign programs can't execute on a Mac, but the Mac could conceivably serve as a conduit for them to reach Windows boxes on the network. I turned on the setting 'Scan external devices when connected' and plugged in a USB drive containing my current set of Windows malware samples.
When nothing happened, I checked with my contact at Airo. He explained that with this setting enabled, the scans you launch include any connected external drives. It doesn't mean that the event of connecting a drive triggers a scan.
With this understanding, I launched a folder scan of the removable device. Airo eliminated 72 percent of the Windows malware samples, which is precisely the average for current products.
It's true that others have done better against Windows malware. Webroot got 100 percent of them, ESET managed 93 percent, and F-Secure Safe (for Mac) detected 91 percent. Again, these samples can't infect a Mac, so detecting them is icing on the cake.
Airo's real-time protection checks any apps you download; it also checks apps on launch. Some products, among them Bitdefender Antivirus for Mac($34.99/Year at Bitdefender), F-Secure, and Sophos, figure this real-time protection is all you need and hence don't bother with scheduled scanning. Airo runs a daily quick scan and a weekly full scan automatically; it doesn't bother to expose the schedule for user-initiated changes. Given that both full and quick scans are plenty fast, this makes perfect sense.
Excellent Lab Test Scores
I've been working with PCs since the 80s, and with Windows-based antivirus tools for many, many years. I'm fully equipped for hands-on testing of Windows antivirus utilities against actual malware samples, even ransomware. But this is a Mac-specific product, and my expertise on macOS is minimal by comparison. That's why test results from independent labs are so important for my Mac antivirus reviews. In fact, when I started reviewing such products, I only chose products with scores from at least one lab.
As you can see in the chart below, the labs don't necessarily keep testing the same set of products. More than 40 percent of the products I track don't have any current lab results. Airo looks very good, with a perfect score from AV-Test Institute. That means it successfully protected the test systems against malware, correctly avoided flagging valid programs or sites as malicious, and did it all without dragging down performance.
Of course, getting top scores from two labs is even better. Avast, AVG, Bitdefender, Kaspersky, and Trend Micro all got perfect scores from both AV-Test and AV-Comparatives.
Quite a few big names, among them ESET, McAfee, and Sophos Home Premium (for Mac), don't have any current test results. For newcomer Airo to hit the scene with one set of perfect scores is impressive.
No Phishing Protection Yet
During Airo's installation I encountered a screen that stated, 'Airo can warn you about deceptive and phishing sites before you visit them.' In response to that offer, I installed browser protection in both Chrome and Firefox to take advantage of phishing protection. I did notice that the settings for the browser extension mentioned blocking sites that contain: Malware, Adware, Scareware, Spyware, and Suspicious. Phishing wasn't listed.
Top Of The Line Antivirus Software Mac 2017
Indeed, when I ran my standard phishing protection test, Airo did not detect or block a single phishing site. Fakes of PayPal, eBay, Amazon, and popular banks slipped right past it. The only page I found that got a reaction was the phishing test page from the AMTSO's collection of antivirus feature tests. Airo detected that one as an adware site.
My contact at the company confirmed that phishing protection is not yet present in Airo, and that the team plans to change the phishing protection promise during install until such time as that feature becomes available. That's good, because it's dangerous to give users a false sense of security by promising protection that isn't actually offered.
An Interesting Arrival
Airo Antivirus for Mac's enthusiastic developers have come up with an attractive new macOS antivirus that does its job unobtrusively. AV-Test Institute put it to the test and awarded the top score in each of three criteria. It wiped out some, but not all, of our Windows malware samples in testing. However, its promised phishing protection isn't yet present. We look forward to the next iteration of this interesting new arrival.
Bitdefender Antivirus for Mac and Kaspersky Internet Security for Mac get top scores from both labs we follow. Both excel in phishing protection, and both include uncommon features such as ransomware protection for Bitdefender and parental controls for Kaspersky. And both cost quite a bit less than Airo. The five-license price of Norton 360 Deluxe (for Mac) is the same as Airo's three-license price, and you can use your Norton licenses on macOS, Windows, Android, and iOS. In addition, your Norton subscription gets you five unlimited licenses for Norton's VPN and 50GB of online storage for your (Windows) backups. These three products are our Editors' Choice picks for Mac antivirus.